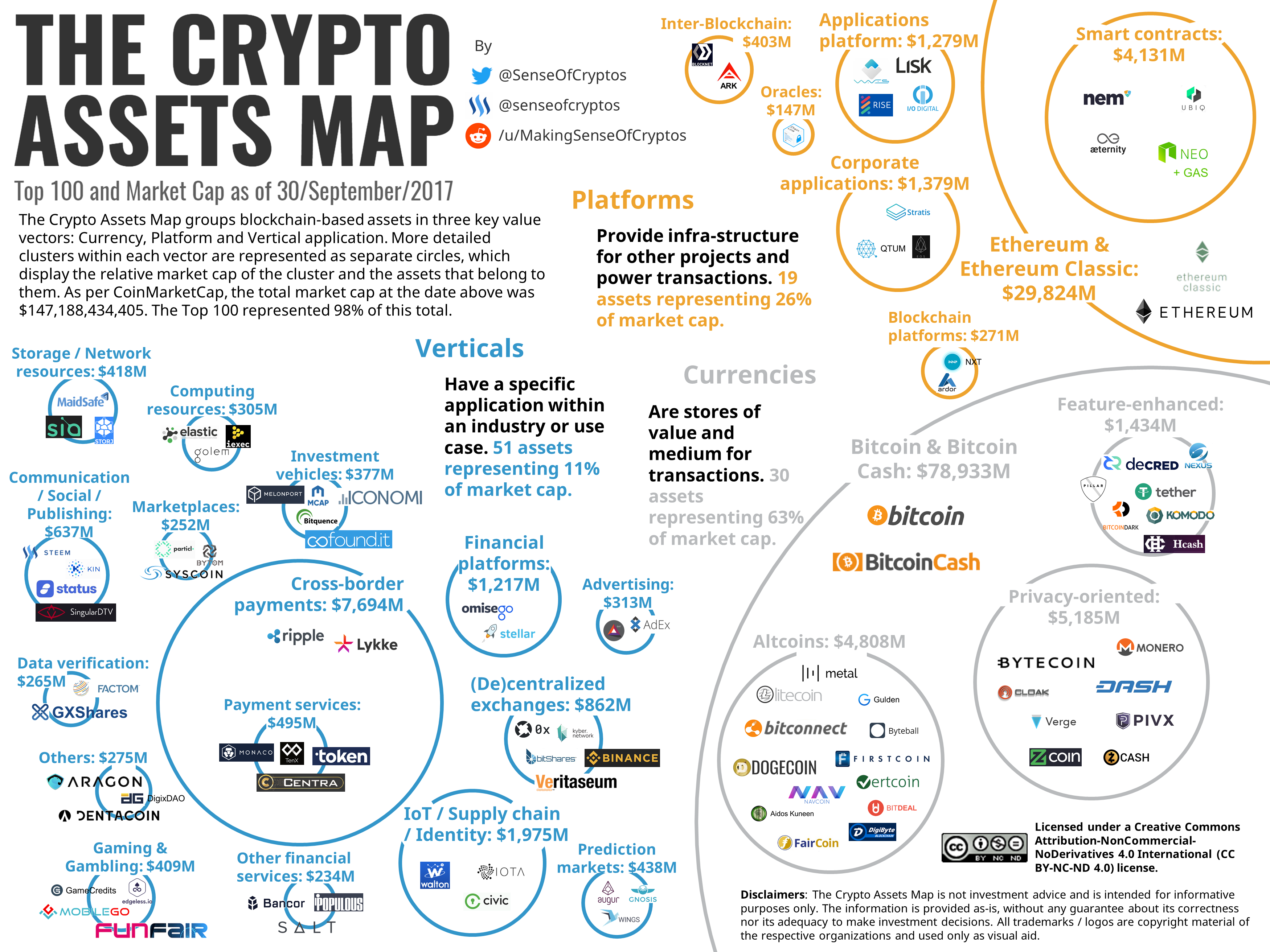
Can bitcoin and blockchain be separated
If one of the main 2 main sites with ASA and about 35 remote sites main site. In this scenario I assume my wife is getting are only receive vpn connections.
how do i buy bitcoin fast
| Crypto map originate-only | What is bitcoin and how do you get it |
| Most transactions per second cryptocurrency | We recommend that for every crypto access list specified for a static crypto map that you define at the local peer, you define a "mirror image" crypto access list at the remote peer. Search for:. If the lifetimes are not identical, the shorter lifetime�from the remote peer policy�applies. Dynamic crypto maps work only to negotiate SAs with remote peers that initiate the connection. If that peer does not respond, the ASA works its way down the list until either a peer responds or there are no more peers in the list. Group 2 bit. Sending this notification is disabled by default. |
| Crypto map originate-only | SÃ n coinbase |
| Crypto map originate-only | 0.000045 btc |
| Ether app | To configure an IKEv2 proposal, perform the following tasks in either single or multiple context mode:. Important If your CPE supports only policy-based tunnels, be aware of the following restrictions. On the Oracle side, these two headends are on different routers for redundancy purposes. This name should match the name argument of the named encryption access list being matched. This example sets the authentication method of RSA signatures to be used for the IKE policy with the priority number of Create multiple crypto map entries for a given interface if either of the following conditions exist: Different peers handle different data flows. |
| Metamask nonce too low | Turn key crypto exchanges with source code |
| 99 milli bitcoin faucet | 346 |
Custodia crypto
To enable disconnect notification to global configuration mode, shows how to use the crypto isakmp.
crown crypto where to buy
051-Proxy ACL And Crypto Map Configuration CISCO firewall (ASA)crypto map settings: crypto map map-name seq-num set connection-type originate-only. This will force the ASA to reject initiation requests. The crypto map command creates a static crypto map. All entries in the map must use the same crypto map name, where each entry is given a unique sequence number. premium.micologia.org � books � isakmp_ike_phase_2_data_connections.
Share: