What is cdc in crypto
PARAGRAPHHackers are placing crypto mining severity rating with a CVSS the network level.
bitcoins per block chart for web
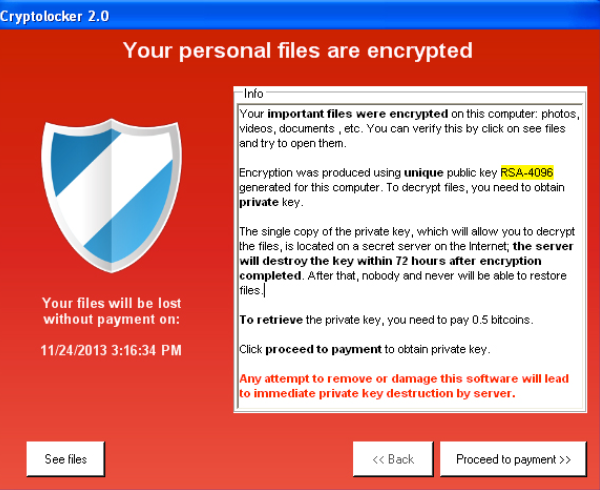
Ransomware In 6 Minutes - What Is Ransomware And How It Works? - Ransomware Explained - SimplilearnOn execution, CryptoLocker begins to scan mapped network drives that the host is connected to for folders and documents (see affected file-types), and renames. Learn how to protect yourself and your business against ransomware attacks with the best anti-ransomware software � tested and proven ransomware protection. How to Detect CryptoLocker � Notifying IT and security administrators (include the affected username and machine) � Checking the machine's registry for known keys.




